This article is designed for IT professionals, cybersecurity enthusiasts, and individuals interested in understanding the complexities of ransomware attacks, particularly WastedLocker. Readers will benefit from gaining insights into the workings of this sophisticated ransomware variant, its impact on large corporations, and actionable steps to protect against such threats. Introduction to WastedLocker Ransomware In the ever-evolving
This article is designed for IT professionals, cybersecurity enthusiasts, and individuals interested in understanding the complexities of ransomware attacks, particularly WastedLocker. Readers will benefit from gaining insights into the workings of this sophisticated ransomware variant, its impact on large corporations, and actionable steps to protect against such threats.
Introduction to WastedLocker Ransomware
In the ever-evolving landscape of cyber threats, ransomware stands out as a particularly insidious menace. From its humble beginnings with the 1989 PC Cyborg demanding a modest $189 ransom, ransomware has morphed into a sophisticated adversary. Among its contemporary variants, WastedLocker reigns as a complex and potent ransomware strain. This article embarks on a journey to decode the intricacies of WastedLocker, shedding light on its origins, mode of operation, high-profile attacks, and the emergence of its Hades variant. Moreover, readers will gain actionable insights into safeguarding their organizations against such malicious threats.
An Inside Look at WastedLocker’s Modus Operandi
In the annals of cybercriminal activity, WastedLocker stands as a creation of the notorious hacker group Evil Corp, notorious for its connections to Russian intelligence agencies. The malware’s journey began in early 2020, using SocGholish, a Remote Access Trojan (RAT), to deceive victims into downloading malicious files masquerading as browser or Flash updates. Once inside a victim’s system, WastedLocker employs a formidable blend of encryption algorithms, including the Advanced Encryption Standard (AES) and the RSA encryption algorithm. This duo renders decryption nearly impossible without access to the hackers’ private keys. As a nod to internet culture, the encrypted files bear the “wasted” appendage, paying homage to the Grand Theft Auto video game series.
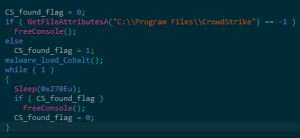
Image by:https://research.nccgroup.com/
High-Profile Targets and Devastating Consequences
WastedLocker’s impact resonates strongly in its choice of targets. Large corporations, household names, and Fortune 500 companies have all found themselves in the crosshairs of this formidable ransomware variant. Symantec’s discovery of 31 WastedLocker attacks on US-based companies in June 2020 underscores the extent of its reach. Sectors such as manufacturing, information technology, and media have all been targeted. Perhaps the most striking example is the attack on Garmin—a prominent GPS and fitness-tracker company. The assault disrupted services, call centers, and production lines, prompting a reported $10 million ransom payment for system restoration. This incident highlights the gravity of WastedLocker’s potential damage.

Image by:https://www.pcrisk.com/
Hades Variant: A New Face of WastedLocker
In the ever-evolving arms race between cybercriminals and cybersecurity experts, innovation remains paramount. Enter the Hades variant—an offshoot of WastedLocker that showcases evolving tactics. While fundamentally a 64-bit compiled variant, Hades introduces novel approaches. Diverging from WastedLocker’s practice, Hades generates a single ransom note and stores crucial information in encrypted files, not the ransom note itself. Furthermore, it directs victims to Tor sites, offering them a free decryption of a single file to prove the effectiveness of their decryption tools. This variant exemplifies the adaptability of cybercriminals and underscores the dynamic nature of the threat landscape.
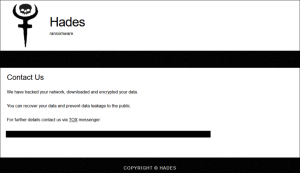
Image by:https://www.crowdstrike.com/
Defensive Measures Against WastedLocker and Beyond
As organizations confront the looming specter of ransomware attacks, proactive defense becomes imperative. Protecting against ransomware demands a multifaceted approach. Robust ransomware protection tools stand as the first line of defense, coupled with stringent software updates to thwart known vulnerabilities. The ability of sophisticated variants like WastedLocker to traverse networks emphasizes the significance of maintaining offline backups. Yet, the human factor remains pivotal—educating employees about cybersecurity best practices fortifies an organization’s resilience.
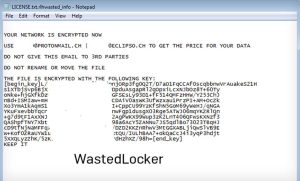
Image by:https://www.bankinfosecurity.com/
Conclusion: Safeguarding the Digital Frontier
In the realm of cybersecurity, the rise of ransomware variants like WastedLocker highlights the ever-present need for vigilance. The evolution from the rudimentary PC Cyborg to the intricate WastedLocker underscores the relentless innovation within the cybercriminal ecosystem. Understanding the mechanics of WastedLocker and its Hades variant empowers organizations and individuals to mount a robust defense against these threats. Through investing in protective measures, staying informed about evolving tactics, and fostering a culture of cybersecurity awareness, we can collectively safeguard the digital landscape and navigate the intricate web of modern threats.

















Leave a Comment
Your email address will not be published. Required fields are marked with *